What is Zero Trust Security? Understanding the Zero Trust Model for the Cloud

Introduction
Purpose of the Article
Zero-trust Security is crucial for modern cloud environments. This article explains the origin of the zero-trust concept. It also covers its impact on protecting digital assets.
Relevance
As cloud services grow, so do security threats. Enterprises must address them. Zero Trust security policies are key to fixing businesses’ weaknesses.
Key Points
Readers will gain insights into:
- The Principles of Zero Trust Security
- Steps to implement it
- Its benefits
- Real-world use cases in cloud environments
What is Zero Trust Security?
Definition
No, Trust Security is a cyber security policy. It is based on the idea of never trusting and consistently verifying. It keeps every user authenticated and monitored, protecting their device or app.
Origins
In the early 2000s, traditional network security models had limits, leading to the new idea of Zero Trust. This concept was popularized by a highly cited Forrester Research study and adopted mainly by organizations that needed reliable cybersecurity.
Core Idea
The system’s foundation is Zero Trust Security, and its ethos is “never trust, always verify.” The system connects only thoroughly verified objects, regardless of their origin.

Why is Zero Trust Important for Cloud Security?
Challenges in Cloud Security
Cloud ecosystems are vulnerable to the following:
- Unauthorized access
- Misconfigurations
- Data breaches
Zero Trust in the Cloud
Zero Trust lessens the risks of these by:
- Enforcing strict identity verification
- Monitoring access continuously
- Restricting lateral movement within the network
Data Protection
Zero Trust protects sensitive data with encryption, access control, and 24/7 monitoring.
Fundamental Concepts of Zero Trust Security
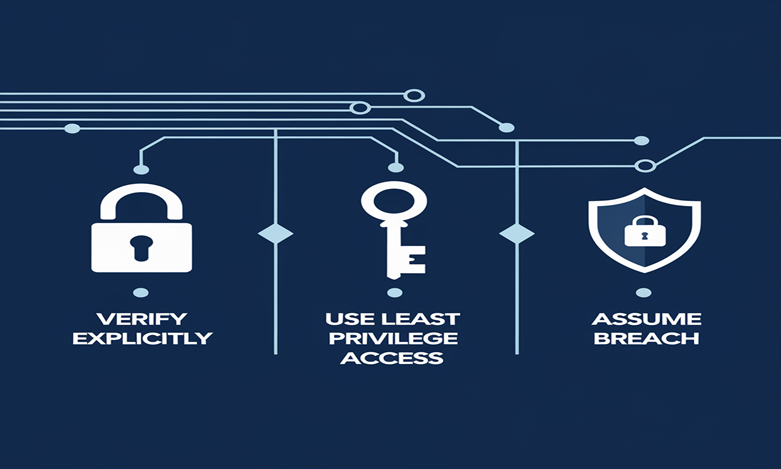
Principle 1: Verify Explicitly
Explanation: Entities, devices, and access requests must be continuously confirmed. Examples include multi factor authentication (MFA) and device trust mechanisms.
Principle 2: Use Least Privilege Access
Explanation: Allow users and devices access to only the resources they need. Implementation: Role-based access control (RBAC) and just-in-time (JIT) access policies.
Principle 3: Assume Breach
Explanation: I think breaches will be inevitable. Strategies: Network segmentation, continuous monitoring, and rapid incident response.
Benefits of Zero Trust Security in the Cloud
Enhanced Data Security
Encryption and strict access controls ensure Zero Trust security. They protect information in sensitive areas. An example is encrypting data at rest and in transit.
Improved Threat Detection
Explanation: Zero Trust relies on quick monitoring for abnormal events. This enables a fast and accurate response to any detected issues. An example is applying AI and machine learning to discern threats.

Simplified Compliance
Explanation: Some industries have specific compliance regulations. Blockchain is a good tool for transparency in processes and, hence, banks. It ensures audits are less time-consuming and keeps the internal access rights of the responsible personnel up to date.
Implementing Zero Trust Security
Step 1: Identifying Critical Assets
Explanation: Find and rank susceptible assets and act accordingly to protect them. An example is listing sensitive data, applications, and user roles.
Step 2: Establishing Identity and Access Management (IAM)
Explanation: Implement strict IAM policies allowing only authorized users to access the app. Example: Employ single sign-on (SSO) and multifactor authentication (MFA).
Step 3: Network Segmentation
Find a network. Then, split it into manageable, monitorable parts to limit lateral movement. Implementing micro-segmentation strategies is a crucial example.
Step 4: Continuous Monitoring and Analytics
Explanation: The system’s traffic should be watched closely for anomalies. Analyze any abnormal network behaviour. An example is applying security information and event management (SIEM) tools.
Everyday Use Cases for Zero Trust Security

Remote Work Environments
Explanation: Ensure that remote employees can securely access the company’s systems and data. A Sample Case: Implement cyber Security to protect ISecuritySaaS tools and security policies.
Protecting Hybrid Cloud Infrastructures
Explanation: Secures data exchanges between on-premises and cloud systems. Example: Zero Trust in multi-cloud setups.
Safeguarding Sensitive Data
Explanation: Zero-trust principles restrict access to sensitive data. Only authorized personnel can access it, including encryption and access controls.
Why Do Companies Need Zero Trust in a Cloud Environment?
In today’s digital world, companies must implement a zero-trust strategy to protect their assets in a cloud environment. Old security methods rely on a network perimeter. Hackers exploit this with remote work and cloud use.
A zero-trust system reminds us that secure methods rely on trust. No user or device should be trusted based on their location. A zero-trust security policy limits access to apps and resources. It uses the principle of least privilege based on user roles.
A security strategy must include zero-trust network access. It must also use strong security measures to improve Security. Using a zero-trust security framework, organizations can ensure strong Security. This architecture will adapt to evoSecurityreats.
Cloud zero trust enables many zero trust use cases. They will protect the organization’s data and Security. Due to the continuous development of security services, the prov, zero-zero-zero, is to meet modern security needs.
A user-friendly method and strict security controls can be used. They can secure a safe and agile production environment.

Why Choose Zero Trust Cloud Security?
Zero trust is a security strategy that brings a new level of creativity to Network Security. It fosters the belief that all entities, inside and outside the Security Centre, are untrustworthy. A cloud solution can change an organization’s architecture, cut costs, and secure its infrastructure.
Zero trust also propagates the oversupply of predictable zero-trust alignment strategies. These strategies ensure that all access requests are well-authenticated and clearly explained. They also confirm access according to the principle of minimal privilege. This zero-trust strategy drives the development of security functions in cloud environments.
The best zero-trust security system limits risks with zero-trust access controls. It is a promising approach to Security in today’s digital world. A zero-tru Security protects data and establishes a strong security model. It verifies the user’s identity throughout their work.

Challenges in Adopting Zero Trust Security
Complexity in Implementation
Explaining: It calls for a rigorous plan and high expertise. Example: The example could be creating identity verification systems and segmentation strategies.
Cost of Deployment
Explanation: Initial high costs of purchasing the required tools, training, and technology. Example: ROI is obtained through increased Security over time.
Resistance to Change
Security: The organization’s employees will generate Security by adopting new habits. Examples: enSecurityemployees in training and modifying workflow.
Opportunities for Zero Trust Security
The future of zero-trust Security is the progress of zero-trust architecture and its use in various environments. By implementing a zero-trust method, companies can ensure secure access to workloads in the public cloud and private network environments, thus diminishing the danger of attackers due to vulnerabilities.
As companies switch to the cloud, the zero-trust approach becomes necessary. Zero trust and zero trust for the cloud allow a more secure solution that prioritizes personal experience while fulfilling zero trust policies. This security model is a zero-trust framework. It shifts away from traditional security methods.
An effective zero-trust security strategy can help organizations safely navigate their data centre resources. By strictly following zero-trust rules, companies can build a better, more secure zero-trust system. Interacting with cloud service providers is key to ensuring a zero-trust solution.
Conclusion
Zero-trust Security is indispensable for protecting cloud environments and combating modern cybersecurity threats. It means that security trust always “rifies” the data. This helps sustain Security and comply with “the GDPR.”
FAQs
What is the Zero Trust Security model?
The zero-trust strategy revolves around “rind “, never trust, always “verify.” This “security framework” assumes no user or device is trustworthy, not even an organization’s network. As part of the zero-trust journey, organizations must implement strong security policies.
Zero trust limits access to users and devices and requires verifying every access attempt. It also requires a strong security stack, which must use hardware-based security and cloud platforms. This is vital for zero trust in hybrid cloud environments. To learn more about zero-trust organizations, one must understand their main principles.
How does Zero Trust Security work in the cloud?
In a cloud environment, zero trust architecture is a foundational security solution. This zero-trust approach operates on the principle that trust is a security model, asserting that no user or device should be automatically trusted, regardless of location. Instead, zero-trust network access ensures secure application access through continuous verification.
The zero trust framework enhances an organization’s security posture by applying trust principles across the cloud. By implementing a comprehensive security architecture, businesses can adopt an effective zero-trust strategy, ensuring that every access request is evaluated based on contextual information.
What are the main benefits of Zero Trust Security?
Zero trust security shifts to a complete focus on Security. It does so by assuming there is no security verifying everything. It allows for continuous authentication and authorization of all users and devices, both internal and external, in the security environment. With zero trust, companies can reduce the risk of data breaches and improve Security.
Is Zero Trust Security complex to Security?
Morganizationsions may find implementing a zero-trust security system to be secure. The key is never to trust anyone, especially new staff. So, we must completely restructure our security protocols and systems.
It requires constant scanning, strict access controls, and a mindset shift. Employees must recognize the value of high-security ethics. Companies need time and money to implement absolute zero trust.

Hello Readers! I’m Mr. Sum, a tech-focused content writer, who actively tracks trending topics to bring readers the latest insights. From innovative gadgets to breakthrough technology, my articles aim to keep audiences informed and excited about what’s new in tech.