Top Cybersecurity Trends to Watch for 2025 and Beyond
1. Introduction
Cybersecurity today is so vital in the digital world. Cyber threats, which are emerging every year, have increased, and being more dependent on technology has resulted in the necessity of the protection of our data and systems.
In 2024, there was a global cyberattack increase of 35%, and there is the strongest belief that 2025 will be the year of escalated threats. Thus, ignorance of Cybersecurity will be detrimental to both individuals and businesses, and the latter will not be able to prepare for the scenarios.
Cybersecurity should not be considered a technical aspect; rather, it is expected to help people lead their lives as well as their working domains confidently. We will look at the key cybersecurity trends that are expected to dominate 2025 and how you can be on the front foot.
Stay Ahead of Cybersecurity Threats in 2024 with Splashtop Secure Remote Access
Be at the forefront of cybersecurity threats in 2024 by employing Splashtop Secure Remote Access precautions for safeguarding your home. Having security teams that encounter emerging threats that become more complex means that proactive security is a must. The cybersecurity landscape requires security solutions that match new cybersecurity trends and strategies.
Through the use of enhanced security tools and protocols, companies can improve their cybersecurity posture. Security assessments will discover potential security weaknesses and, thus, make it possible for security teams to avoid any cyber incidents.
Stay up to date on the latest cybersecurity trends to be resilient to evolving cybersecurity threats.
Upcoming Cybersecurity Developments for 2025

Trend #1: AI-Driven Cybersecurity
- Role of AI in Security: A piece technique originally developed for searching for defects in mined data is now being used as a cybersecurity tool to quickly indicate and stop cyberattacks based on the obvious signs. In particular, AI systems can perform tasks such as scanning a network for vulnerabilities, identifying vulnerabilities, and responding to threats in real time.
- Benefits:
- Faster response times.
- Improved accuracy of Threat Identification.
- Automatic security systems upgrades.
Challenge:
- Hackers Using AI: Cybercriminals are now in a position to use AI in order to launch more sophisticated and intelligent attacks.
- High Costs: Artificial intelligence (AI) can be costly to install and sustain; this is why small businesses are unable to pay for them. Hence, AI would be here but not there in the small business space.
- False Positives: Sometimes, AI can mistakenly consider non-harmful activity to be dangerous and, thus, cause unnecessary hiccups.
- Lack of Skilled Professionals: Some companies do not have personnel who, with their experience and knowledge, can masterfully establish AI systems and keep them well-run.
- Adversarial Attacks: Cyber-criminals can manipulate machine learning systems by injecting erroneous data into them, thereby leading to failure in detecting the actual threats.
- Ethical Concerns: AI’s involvement has increased issues of privacy and the data collection process.
Trend #2: Zero Trust Architecture
Zero trust inference connotes that plugs and not only users will have to authenticate their ID before they are simultaneous to the data or systems.
Why it’s important:
- Stops internal threats.
- Makes network security stronger.
- Protects sensitive data even during a breach.
- However, zero-trust security will be used more extensively in various fields in the meantime, in finance and healthcare, in 2025.
Trend #3: Rise of Cloud Security Measures
Since businesses are storing their data in cloud storage more than ever before, it is vital to be sure the data is kept safe.
Top Risks:
- Data breaches through incorrect configurations.
- Cyberattacks on cloud platforms.
Emerging Solutions:
- Better encryption methods.
- Automated tools to detect vulnerabilities.
- Employee training to avoid mistakes.
Trend #4: Challenges in Cloud Security and the Internet of Things (IoT)
- What is IoT? IoT refers to devices such as smart home systems, wearable fitness trackers, and industrial machinery that are connected to the internet.
Risks:
- Hackers attack smart devices.
- IoT breaches in industries which result in major disruptions.
- Best Practices for IoT Security:
- Implement unique, complex passwords for each of the devices.
- Routinely update software.
- Install devices on only secure networks.

Trend #5: Evolution of Ransomware
Ransomware, where the victims are locked out of their system, and the hackers demand money, is becoming more intelligent.
New Tactics:
- Double extortion: Hackers not only encrypt the data, but they also threaten to release it.
- Ransomware-as-a-service: Tools that hackers are able to rent to carry out attacks.
Preventive Measures:
- Regularly back up your data.
- Implement the use of advanced antivirus software.
- Training employees on phishing email recognition is necessary since many such emails are targeted at employees.
Trend #6: Cybersecurity for Remote Workforces
Remote work has been a catalyst of new risks like unsecured Wi-Fi networks and poorly designed personal devices.
Strategies for Protection:
- Make sure the employees are using VPNs (virtual private networks).
- Hand company devices out and make sure those are safe.
- Secure and frequent cybersecurity training for employees.
Trend #7: Cybersecurity Skills Gap and Education
There is a worldwide shortage of skilled cybersecurity professionals.
What’s going On?
- They are building and encouraging programs to promote training.
- Universities and schools are now beginning to add more and more cybersecurity courses.

Trend #8: Quantum Computing and Cryptography
Quantum computing in the future could be the first of its kind in the successful cracking of existing encryption systems, which are used for safeguarding confidential information.
Achievements:
- Post-quantum cryptography is on the verge of being completed by designs to block the attack of this demon.
- Quantum-safe encryption should now be used by businesses to start strategizing their encryption plans for the post-quantum era.
Trend #9: Integration of Cybersecurity with Emerging Tech
The AR, blockchain, and 5G networks have made Cybersecurity more effective than ever before.
Key Points:
- Blockchain development creates systems that cannot be converted.
- 5G is connecting a larger number of devices, which calls for greater security.
- AR adds up to new kinds of threats in gaming and education, which are the industries that have witnessed the influence of AR.
Challenges in the Security of Quantum Computing
Quantum computing development has resulted in a huge set of security challenges that Cybersecurity encounters. As emerging cyber threats grow, the existing defense mechanisms for sensitive data may also become useless.
The great cybersecurity experts are getting more into changing cybersecurity strategies in order to make the firm more secure against these threats. In the future, understanding security trends will be a crucial tool.
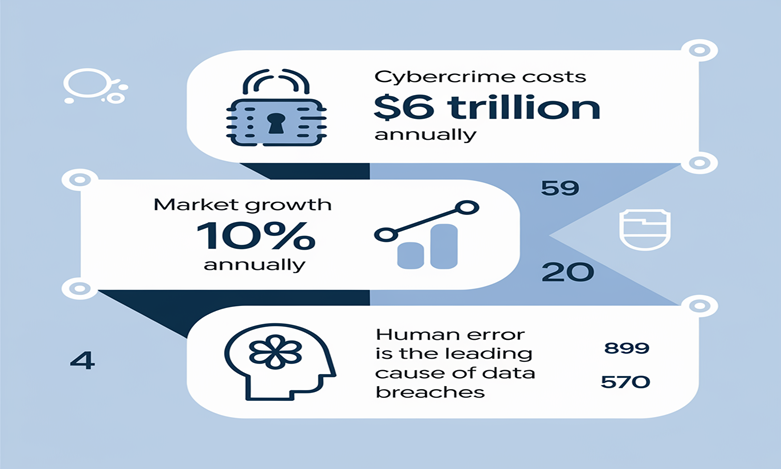
Fast Facts about the Cybersecurity Industry
- It is expected that the total loss from cybercrime worldwide will be $10.5 trillion per year by 2025.
- The cybersecurity market is said to grow by 12% annually; this means that the sector is becoming essential.
- More than 80% of breaches are due to human mistakes, which underlines the importance of training and education.
Industry-Specific Cybersecurity Challenges
Healthcare Sector
- Hospital assaults with a ransomware scheme threaten patients’ health care and are a serious privacy issue for their medical data.
- More and more medical devices, such as pacemakers, are being targeted.
Financial Services
- Digital banking struggles with threats such as fraud, phishing scams, and money laundering.
- Financial institutions are governed by strict regulatory measures to ensure the safety of their customers’ data.
Small Businesses
- Small companies typically have a limited budget, which makes it difficult for them to procure advanced cybersecurity systems.
- Since they have rather weak cyber defenses, they are favored among hackers.
Adopting a Proactive Stance with Predictive Cybersecurity Measures
Adopting a proactive stance with predictive cybersecurity measures is crucial as new threats continue to become more sophisticated. Organizations must implement proactive security measures to safeguard sensitive information and strengthen their security posture against prevalent cybersecurity threats.
By focusing on emerging trends and emerging cybersecurity trends, businesses can enhance their security operations and introduce new cybersecurity protocols. A robust culture of cybersecurity awareness plays a critical role in Cybersecurity, ensuring that all employees understand the importance of Cybersecurity.
As the cybersecurity workforce evolves, a growing demand for skilled cybersecurity professionals equipped to detect and respond to cyber threats is growing. This shift will significantly impact the future of Cybersecurity, necessitating a comprehensive approach to Cybersecurity that integrates traditional and innovative security measures to protect digital assets.
Revised Safety Guidelines
New Security Regulations are the most effective approach to handling the security threats that today’s digital environment comes along with. In the digital world, cybersecurity cybersecurity. Therefore, trends in Cybersecurity are reshaping the overall cybersecurity posture of organizations worldwide. The cybersecurity trends of 2024 will launch fresh cybersecurity programs to alleviate past cybersecurity threats.
Security measures are vital to detect and respond to cyberattacks if a breach occurs. Revamped cybersecurity education and the imparting of skills will be game changers in cybersecurity personnel with a solid cybersecurity career. These regulations will have the most effect on the way businesses harmonize their approach to security.
Security in cyberspace is no longer a choice; it is a must. If we stick to 2025 plus instead of a small portion of it, we will be able to know and understand these plans better, eventually being more secure. Due to the success of proactive measures and also obtaining up-to-date knowledge, we are safe from cyber threats while still living in this rapidly changing digital world.

Conclusion
Cybersecurity is no longer optional; it’s a necessity. As we look to 2025 and beyond, understanding these trends can help individuals and businesses protect their digital futures. By adopting proactive measures and staying informed, we can stay ahead of cyber threats in an ever-evolving digital world.
FAQs
What are the key cybersecurity trends for 2025?
Moving forward to 2025, the main cybersecurity trends will be the result of the intensifying global cyber environment. The perception of cyber security has grown because of organizations’ threats and the urge for improvement in their cybersecurity protocols.
As a result of data breaches and cyber threats, CybersecuriCybersecurityghlighted, thus forcing businesses to bolster their security. Demand for skilled cybersecurity personnel will remain on the upward trend, subsequently bringing about a paradigm shift in cybersecurity practices.
What industries face the most cybersecurity threats?
Finance, healthcare, and the critical infrastructure sectors experience the most significant cybersecurity threats. The cybersecurity trends for 2024 will require these sectors to comply with the cybersecurity protocols, which are quite different from those they used earlier, to prevent potential breaches.
In the cybersecurity sector, employee cybersecurity training is a very important part of ensuring Cybersecurity. Organizations need to deCybersecurity to cyber incidents, and they must also intensify their cybersecurity programs to address various dimensions of cybersecurity issues. Traditional cybersecurity techniques will not be enough.
How can businesses prepare for future cybersecurity risks?
In order to prepare for future cyber security threats, businesses should be updated on the most recent trends in cyber security and be aware of new cyber security threats. Organizations are able to pursue this proactive approach in the cyberspace landscape through the development of rigorous defenses backed by just talking about cyber security trends.
What’s more, involvement in Cybersecurity across various departments and tapping into strategic cybersecurity ventures can significantly strengthen overall resilience against current cybersecurity challenges.
What is the impact of quantum computing on Cybersecurity?
The advent of quantum computing poses significant challenges. Its ability to quickly solve complex problems can undeCybersecurityonal encryption methods, rendering them vulnerable. This shift necessitates the development of quantum-resistant algorithms to safeguard sensitive data against potential breaches, reshaping the landscape of digital security.
What are the cybersecurity risks of remote working?
Remote working introduces several cybersecurity risks that organizations must address. First, employees often use personal devices that may lack adequate security measures, increasing vulnerability to attacks. Public Wi-Fi networks can also expose sensitive data to interception, while inadequate employee training can lead to unintentional breaches through phishing or malware.

Hello Readers! I’m Mr. Sum, a tech-focused content writer, who actively tracks trending topics to bring readers the latest insights. From innovative gadgets to breakthrough technology, my articles aim to keep audiences informed and excited about what’s new in tech.