Understanding Zero Trust Architecture: The Security Model You Need

Introduction
In today’s digital world, traditional security models are no longer enough. Cyber threats are becoming more sophisticated, and attackers are finding new ways to bypass outdated security systems. This is where Zero Trust Architecture (ZTA) comes in—a modern security model designed to protect organizations from cyber threats. Unlike traditional perimeter-based security, which assumes everything inside a network is safe, Zero Trust operates on the principle of “never trust, always verify.”
Zero Trust ensures that every request for access is verified before granting permissions. Organizations must authenticate and authorize every user, device, and network request, minimizing security risks. Many companies are now shifting towards this approach to strengthen their cybersecurity. With remote work and cloud adoption growing rapidly, implementing Zero Trust has become a necessity rather than an option.
History of Zero Trust Security Model
The concept of Zero Trust, first introduced by John Kindervag, a security analyst at Forrester Research, in 2010, marked the beginning of organizations recognizing the importance of zero trust principles. He argued that organizations should assume that all network traffic—inside or outside the network—is untrusted. Instead of relying on traditional network perimeters, Kindervag suggested focusing on identity and access management to secure sensitive data thus implementing a zero trust strategy to minimize risks.
Over time, major organizations, including Google, Microsoft, and the U.S. government are leading the way in adopting a zero trust maturity model to protect against security breaches. The Cybersecurity and Infrastructure Security Agency (CISA) has also recommended Zero Trust strategies as a necessary approach to improve security posture.
Notable milestones in the adoption of Zero Trust include Google’s implementation of BeyondCorp in 2014, which eliminated implicit trust and improved security for employees accessing corporate resources remotely. In 2018, the National Institute of Standards and Technology (NIST) developed a formal Zero Trust model, providing a framework for organizations looking to adopt this strategy. By 2021, the U.S. government mandated Zero Trust implementation across federal agencies, solidifying its importance in modern cybersecurity.
Three Principles of Zero Trust Model
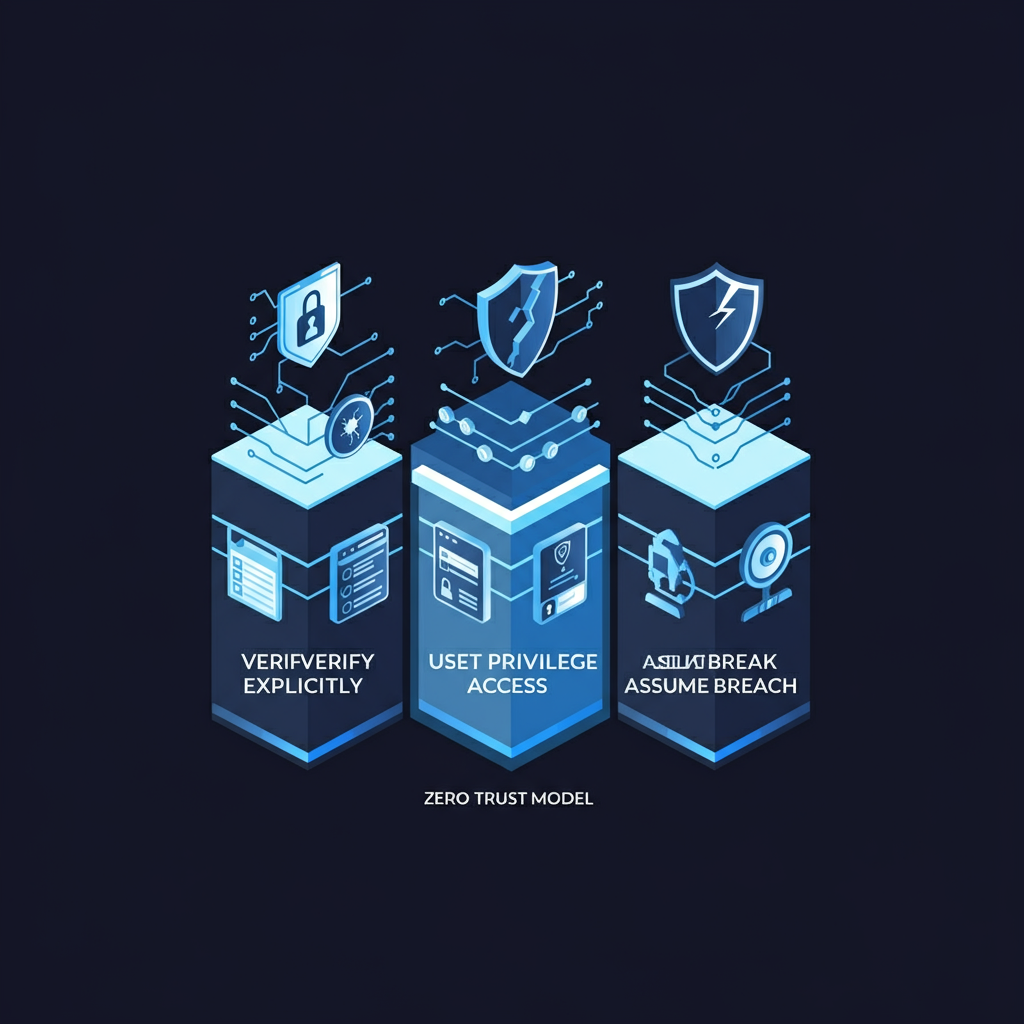
The three core principles of Zero Trust are:
- Never trust, always verify – Every user, device, and request must be authenticated and verified before access is granted.
- Least privilege access – Users and systems should only have access to the minimum resources necessary for their roles.
- Assume breach – Organizations must continuously monitor for threats and take proactive security measures to mitigate potential attacks.
To achieve Zero Trust, organizations should focus on identity and access management (IAM), device security, network security, data security, and security analytics. Implementing a combination of these pillars helps to minimize attack surfaces and prevent unauthorized access.
How Zero Trust Architecture Works

A Zero Trust architecture provides a strong security framework by applying strict authentication and verification measures across an organization. Unlike traditional perimeter-based security, where firewalls protect internal systems, Zero Trust requires security teams to continuously evaluate and verify all access requests; and verifying each request based on all available data before granting access. This approach significantly reduces the risk of unauthorized access and data breaches.
Five Pillars of Zero Trust
Several technologies and strategies form the foundation of Zero Trust security:
- Multi-Factor Authentication (MFA) – Enhances security by requiring multiple authentication factors.
- Microsegmentation – Divides networks into small segments to limit access and reduce attack surfaces, in line with zero trust access.
- Cloud Access Security Broker (CASB) – Ensures secure access to cloud applications and enforces security policies.
- Security Information and Event Management (SIEM) – Provides real-time security monitoring and threat detection.
- Endpoint Detection & Response (EDR) – Detects and mitigates cyber threats on user devices, ensuring continuous monitoring.
How to implement a Zero Trust Security?
Organizations must take a structured approach to implement Zero Trust effectively. The process typically includes the following steps:
- Assess Current Security Posture – Identify gaps in security policies and technologies that could expose vulnerabilities.
- Define Zero Trust Policies – Establish clear security policies for user authentication, data access, and threat detection.
- Deploy Security Controls – Implement identity and access management tools, encryption techniques, and network segmentation.
- Monitor & Improve – Continuously test, evaluate, and refine the Zero Trust implementation strategy to adapt to emerging threats.
Best Practices for Zero Trust Implementation
Organizations implementing Zero Trust should adopt the best practices to ensure a smooth transition and maximum security.
Firstly, enforcing the least privilege access model is crucial. Users and devices should only have access to the minimum resources necessary for their tasks, reducing the risk of internal threats. Additionally, enabling multi-factor authentication (MFA) adds an extra layer of security, ensuring that even if credentials are compromised, unauthorized access is prevented.
Another essential practice is continuous monitoring and real-time threat detection. Cyber threats evolve rapidly, and organizations must proactively monitor all network activities using SIEM and EDR solutions. By utilizing advanced analytics and machine learning, organizations can identify unusual behavior patterns and take immediate action to prevent potential breaches.
Organizations should also focus on device and endpoint security. In a Zero Trust model, all devices—whether company-issued or personal—must be verified and compliant with security policies before gaining access to network resources. Implementing endpoint security solutions ensures that only trusted and secure devices connect to the corporate environment through a zero trust access model.
Lastly, organizations must ensure seamless integration of Zero Trust with existing security infrastructure. Many enterprises already have firewalls, VPNs, and identity management systems in place. Instead of replacing them entirely, Zero Trust should complement and enhance existing security measures, ensuring a smooth transition with minimal disruption.
Benefits of Zero Trust
Adopting Zero Trust security offers several advantages for businesses.
One of the primary benefits is the reduction of data breach risks. By verifying every user, device, and request, Zero Trust eliminates the assumption of trust, ensuring that unauthorized access attempts are blocked before they can cause harm. Additionally, organizations benefit from improved network security, as every access request is authenticated and monitored, significantly reducing exposure to cyber threats.
Zero Trust also enhances operational efficiency. By implementing automated security measures and access controls, IT teams can streamline security operations, reducing the burden of manual threat monitoring. This allows security professionals to focus on proactive threat intelligence rather than reacting to incidents after they occur.
Compliance with data protection regulations such as GDPR, HIPAA, and CCPA is another critical advantage. Zero Trust ensures that organizations implement strict access controls and monitoring, making it easier to meet regulatory requirements and avoid potential fines.
Moreover, Zero Trust is highly adaptable to cloud and hybrid environments. With more organizations shifting to cloud-based services, Zero Trust provides an effective security model that extends protection beyond traditional network boundaries, ensuring robust security across all platforms.
Case Study: Google’s BeyondCorp
Google implemented Zero Trust through its BeyondCorp initiative, eliminating implicit trust and allowing employees to securely access corporate resources from anywhere. This approach has improved Google’s security posture and reduced cyberattack risks. By prioritizing user authentication, endpoint verification, and network segmentation, Google successfully built a scalable and secure Zero Trust framework.
Challenges of Zero Trust Implementation

While Zero Trust is a security model that enhances protection, it also presents challenges:
- Initial costs – Implementing a Zero Trust solution may require significant investment in new technologies.
- Complex implementation – Organizations need to restructure existing security architecture, which can be time-consuming.
- User resistance – Employees may initially find additional security measures inconvenient, leading to resistance.
Overcoming These Challenges
- Start with small-scale Zero Trust initiatives before full deployment.
- Educate employees about the benefits of Zero Trust and how it enhances security.
- Use Zero Trust resources from CISA and NIST for guidance on best practices.
Conclusion
With cyber threats evolving, organizations must move toward Zero Trust to strengthen their security strategy. By following Zero Trust best practices and leveraging Zero Trust networks, businesses can protect their sensitive data, improve their security, and achieve Zero Trust with confidence.
FAQs
What is Zero Trust Architecture?
It’s a security model that means “never trust, always verify,” requiring everyone to prove they are allowed to access information.
Why is Zero Trust important?
It helps protect data by ensuring that no one is trusted automatically, reducing the chance of unauthorized access.
How can my organization implement Zero Trust?
Start by identifying sensitive data, setting access policies, and continuously monitoring network activity.
What are the Zero Trust Resources?
Resources include complex setup, potential impact on user experience, and the cost of implementation.
What is Zero Trust Network Access?
Zero Trust Network Access (ZTNA) is the main technology that enables organizations to implement Zero Trust security. Similar to a software-defined perimeter (SDP), ZTNA conceals most infrastructure and services, setting up one-to-one encrypted connections between devices and the resources they need.

Hi! I’m Muhammad Shahzaib. As a content writer focused on technology, I constantly seek out trending topics to deliver fresh, insightful articles. My goal is to keep readers informed and engaged with the latest and emerging innovations in the tech world.